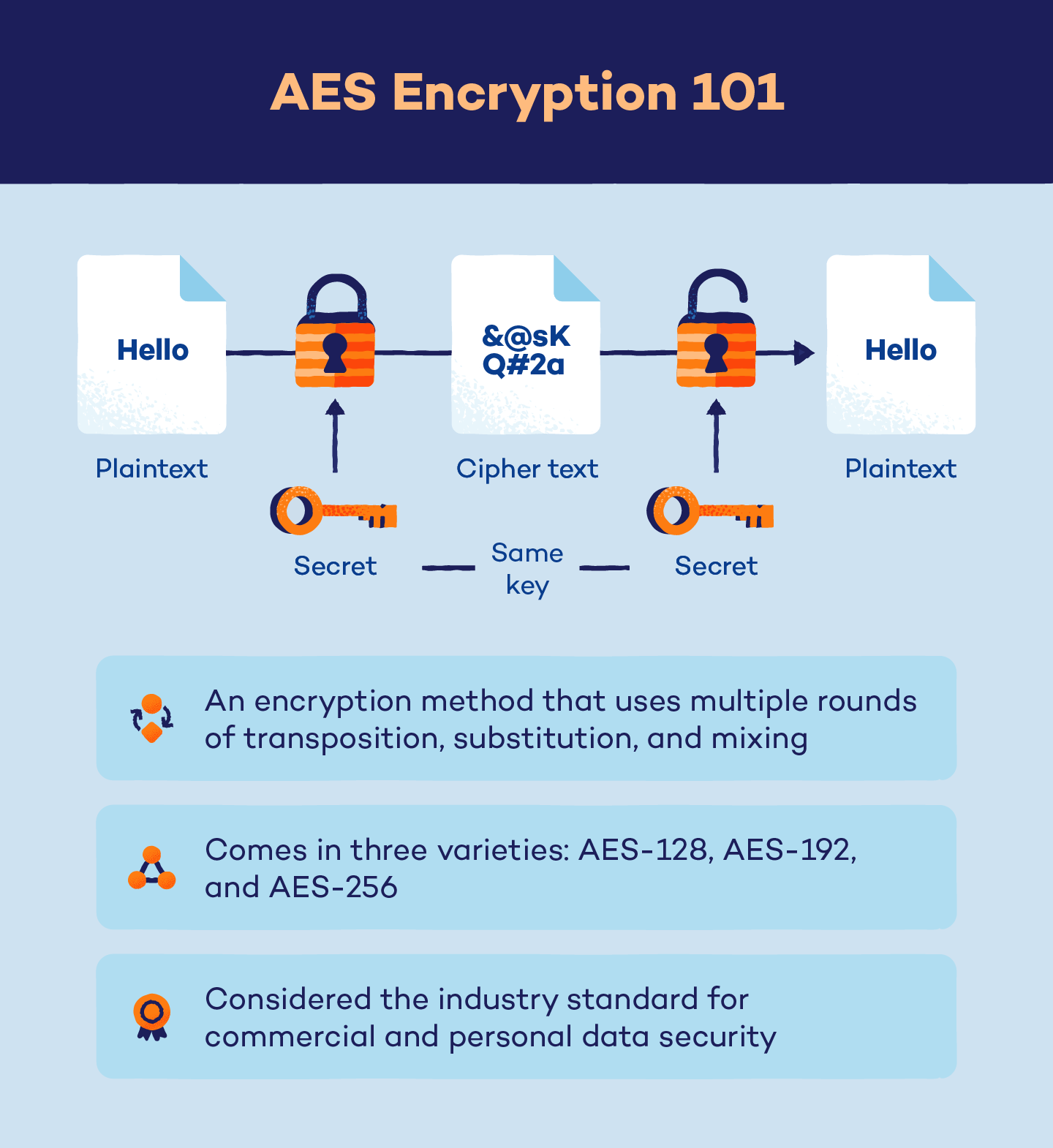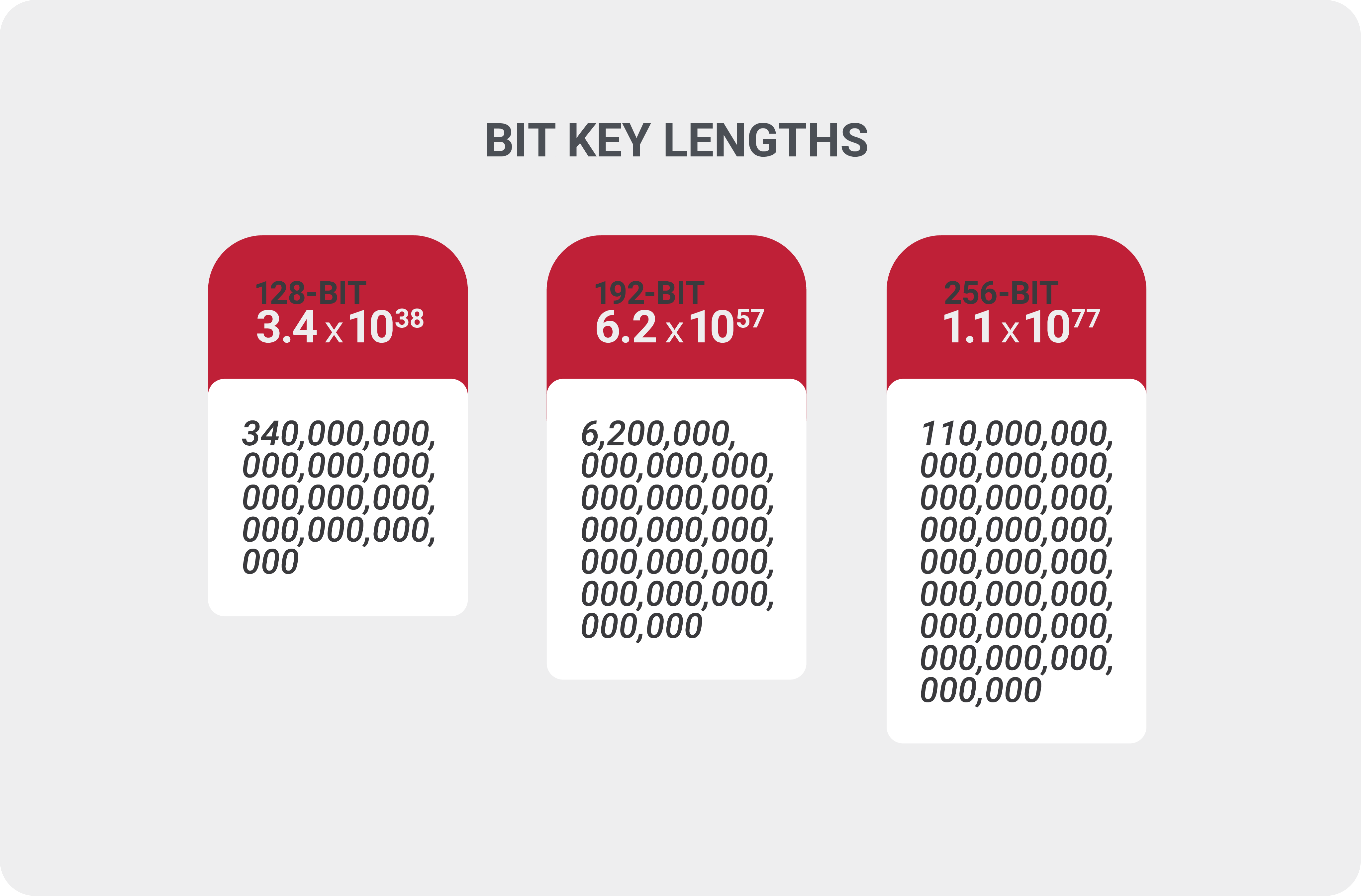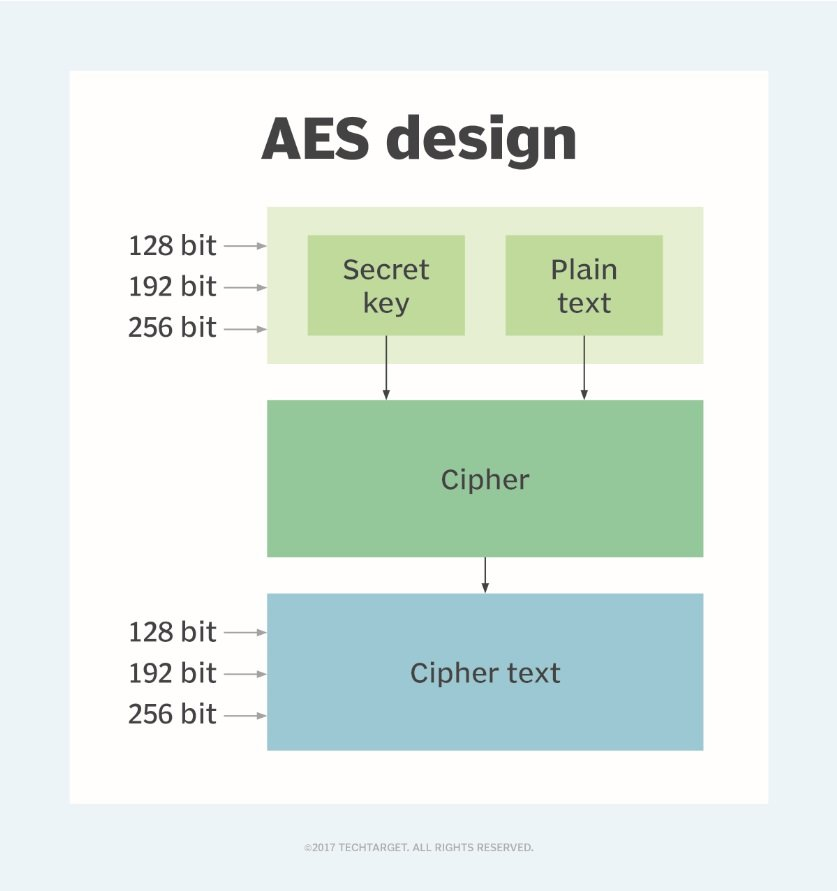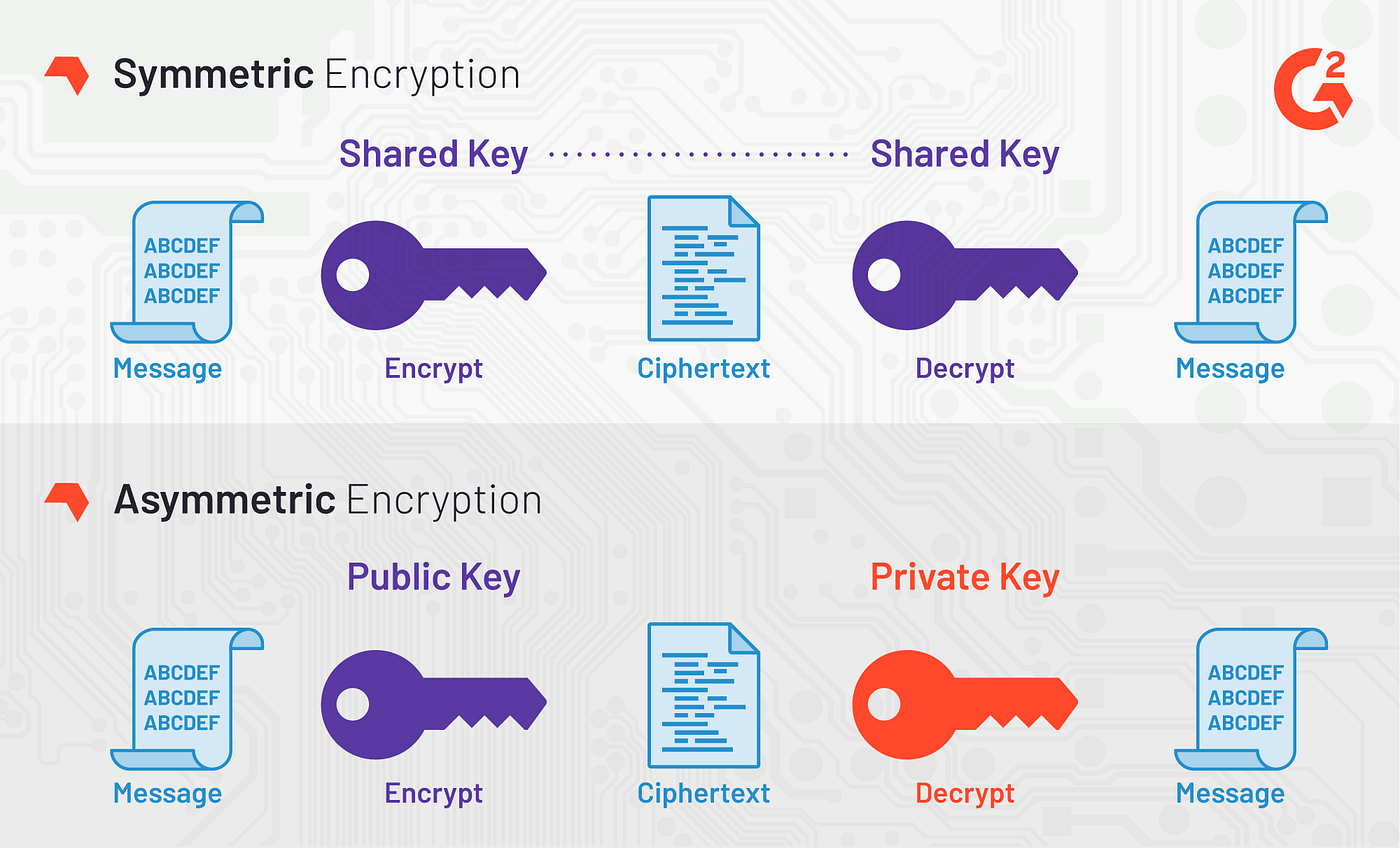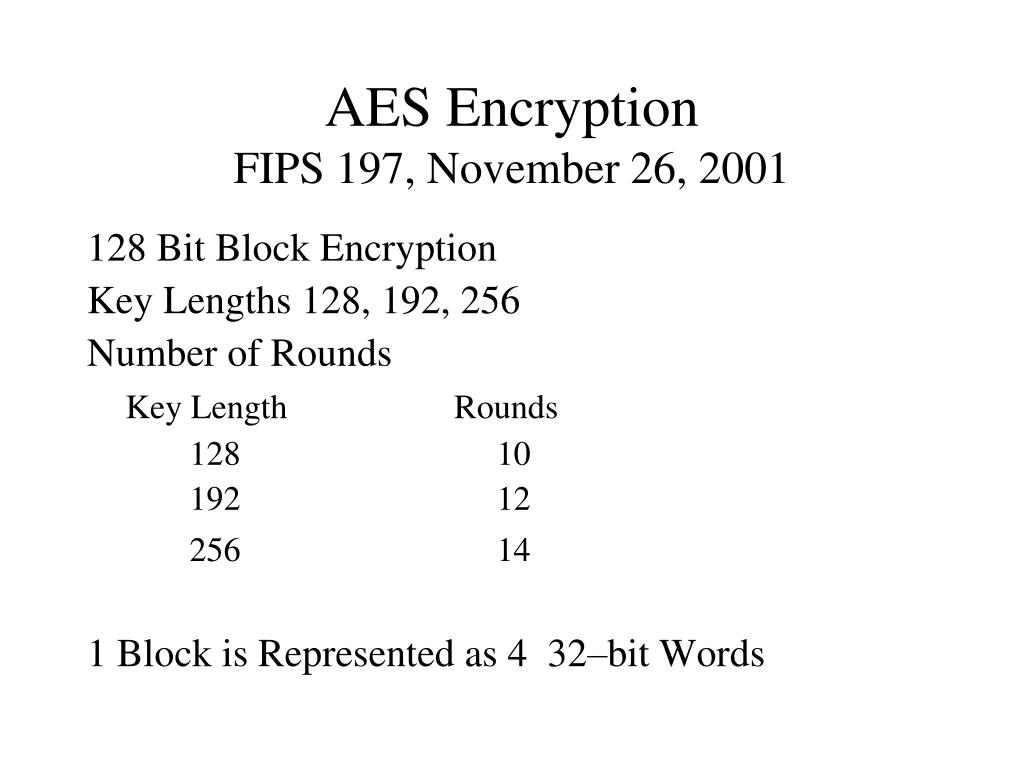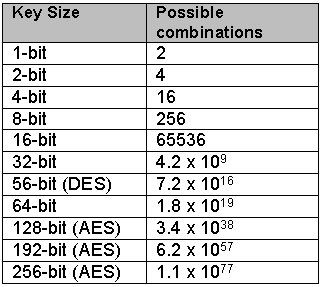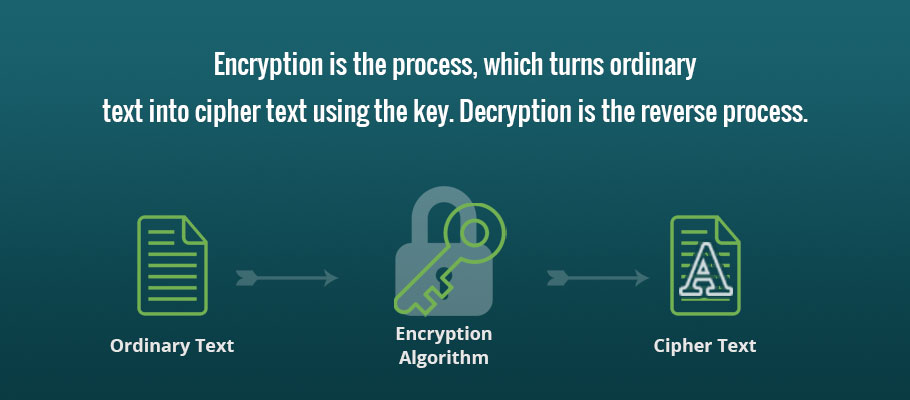
AES Encryption 256 Bit. The encryption standard to rule them… | by Cory Maklin | Towards Data Science

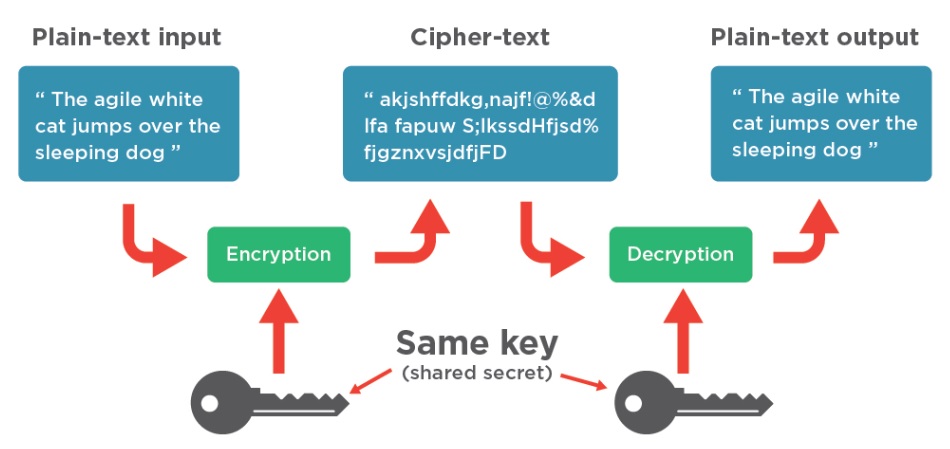
How to solve AES example? | AES Encryption Example | AES solved Example | AES Example solution - YouTube

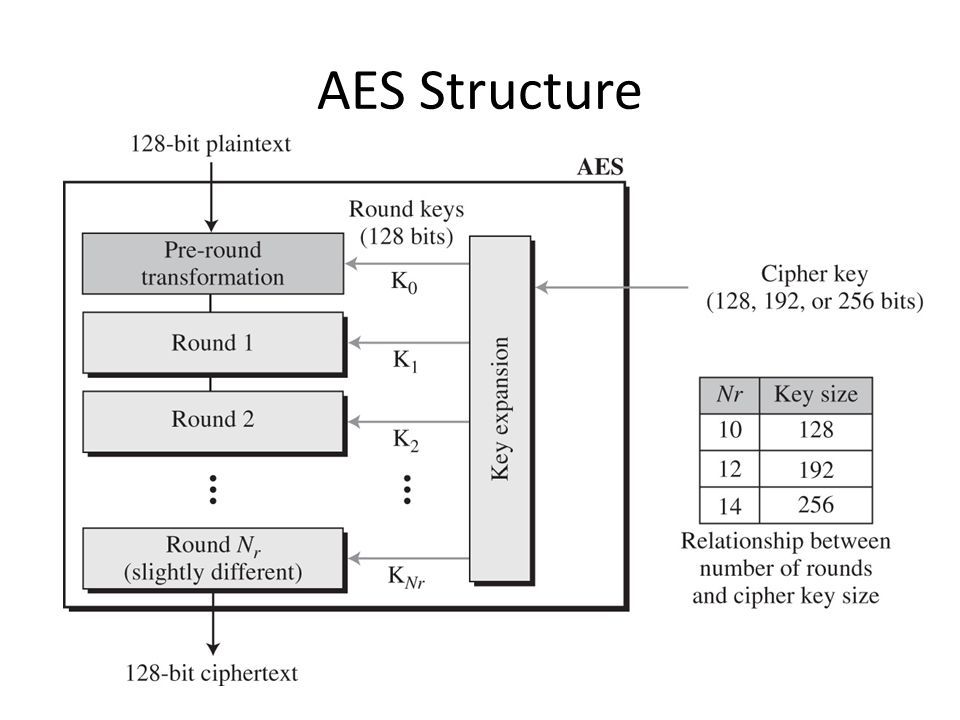
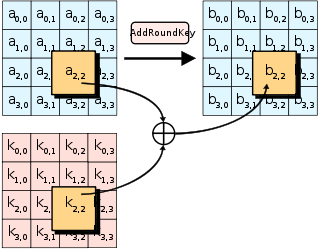
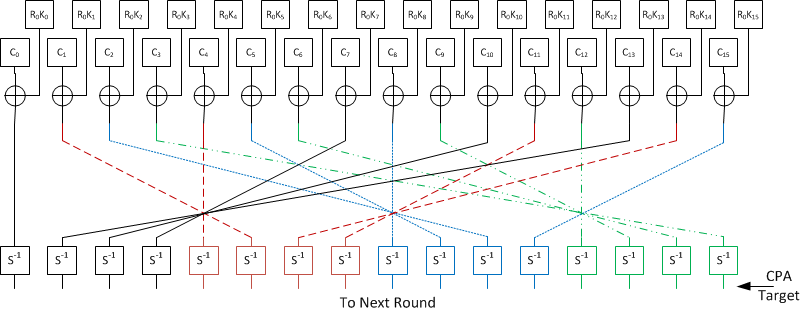
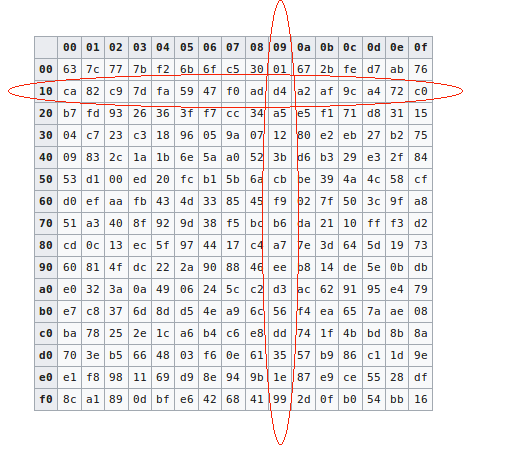
Figure: Structure of AES III. Implementation The AES algorithm is based... | Download Scientific Diagram