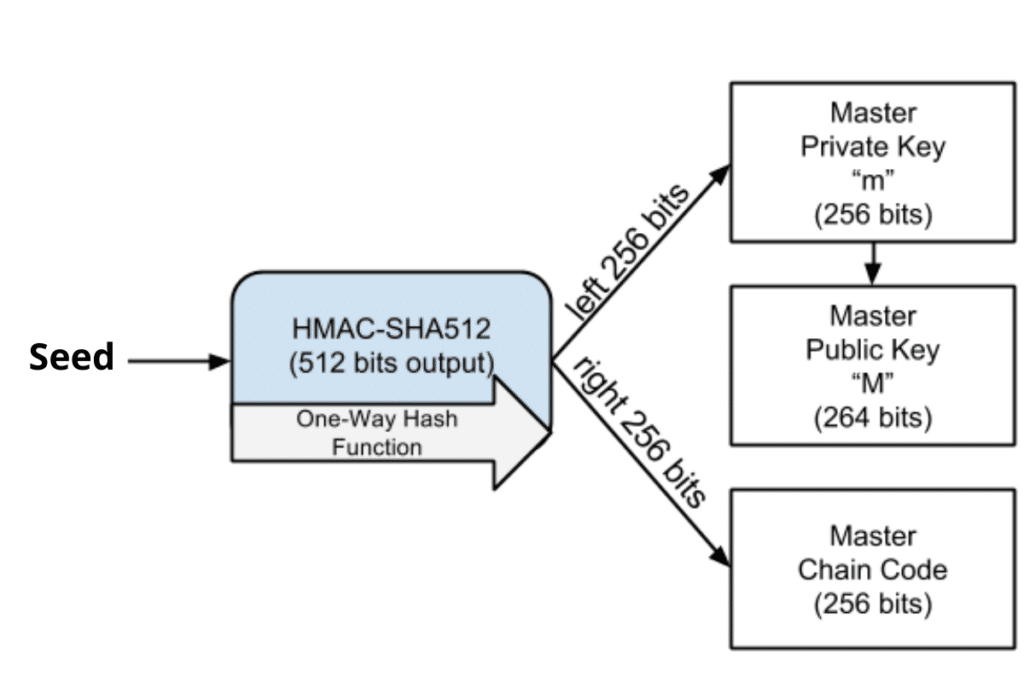
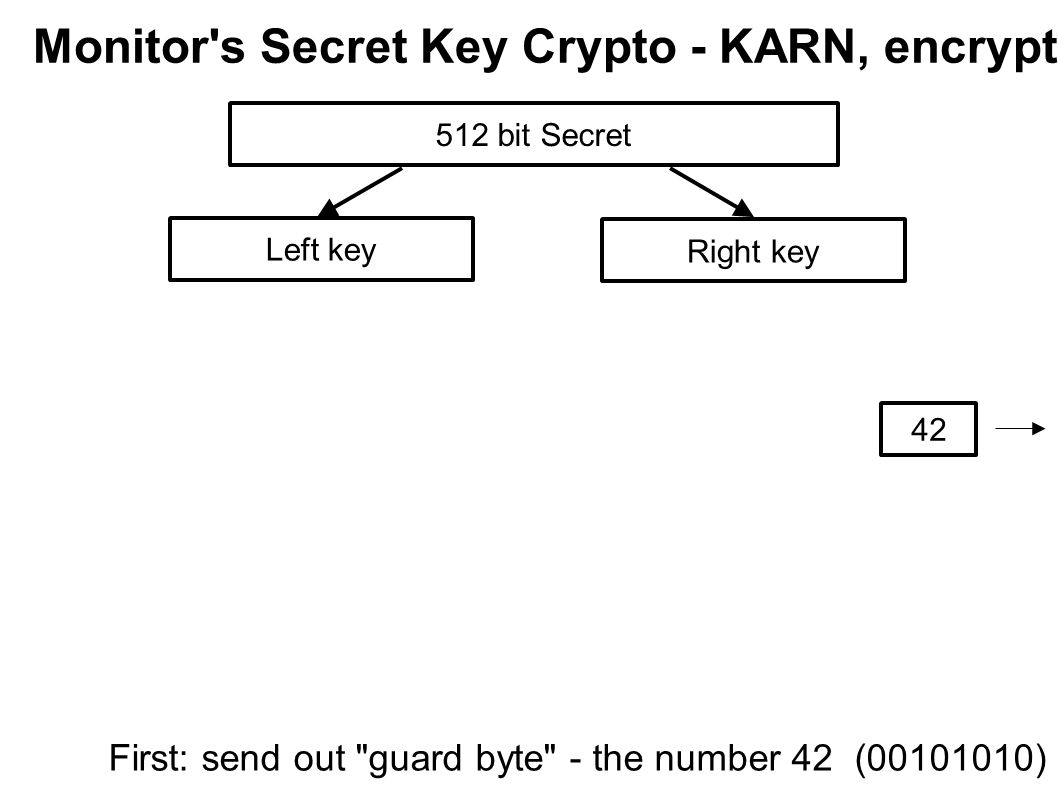
Generation of 512-bit Session Key using fixed κ =5 and different number... | Download Scientific Diagram
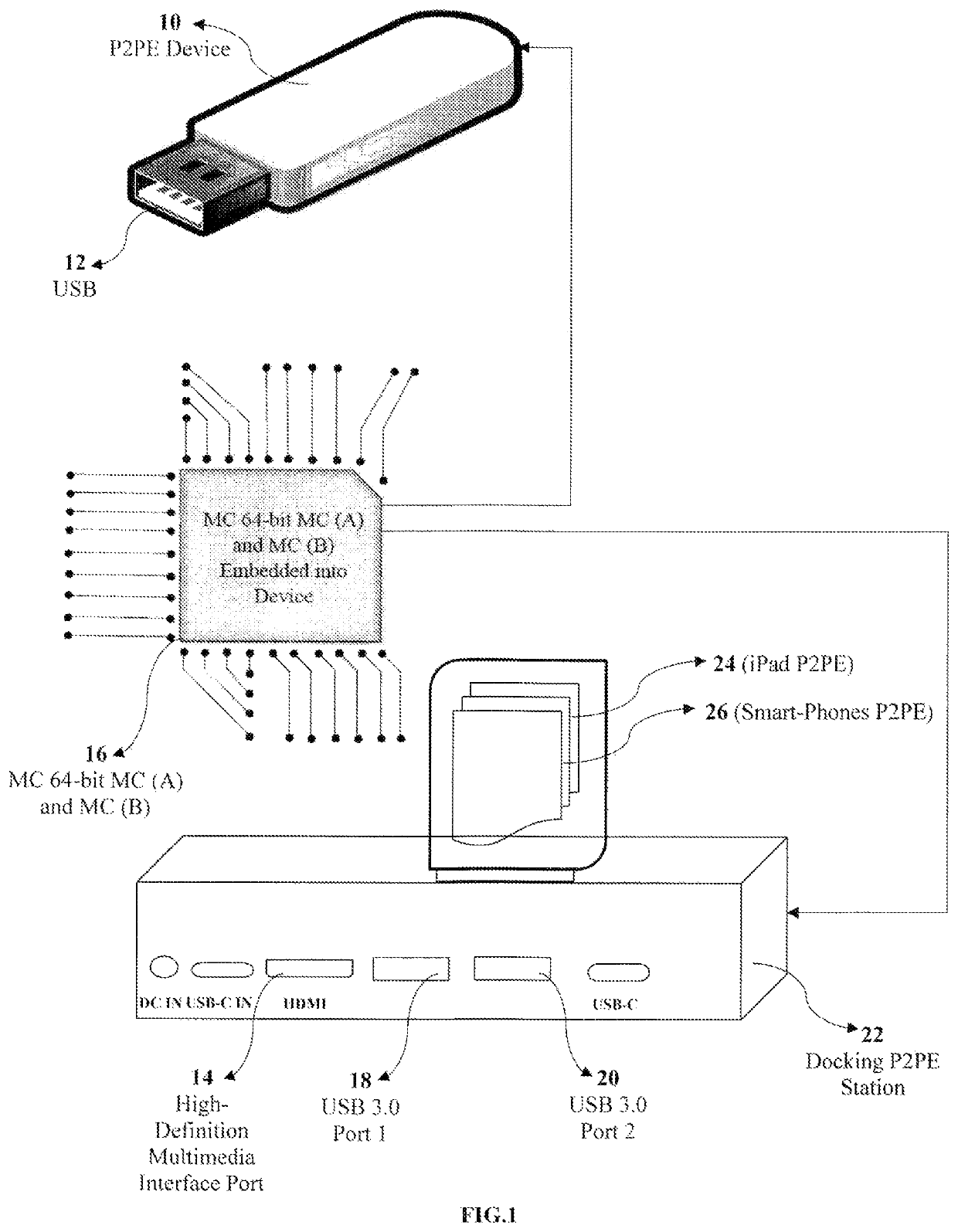
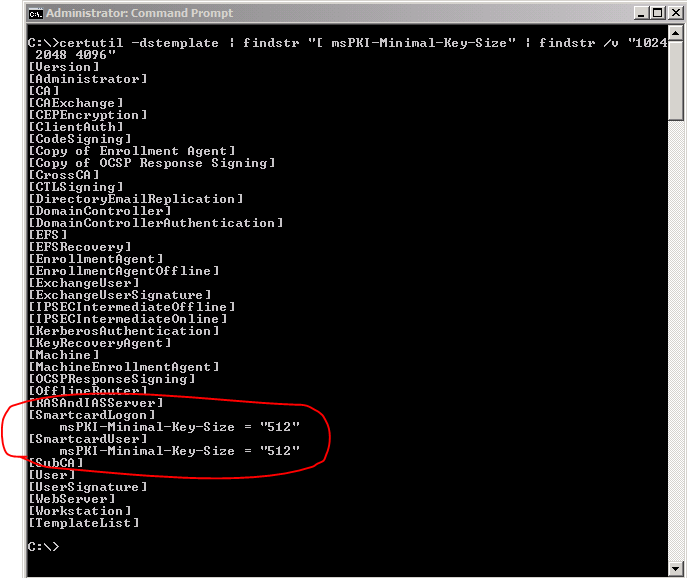
Methods, system and point-to-point encryption device microchip for AES-sea 512-bit key using identity access management utilizing blockchain ecosystem to improve cybersecurity - Eureka | Patsnap

CipherShield 512-bit AES USB-C SSD USB-Powered FIPS 140-2 Level 2 HIPAA USB 3.1 Gen 2/eSATA Hardware Encrypted External Portable Drive | Buslink Buy
![PDF] AES-512: 512-bit Advanced Encryption Standard algorithm design and evaluation | Semantic Scholar PDF] AES-512: 512-bit Advanced Encryption Standard algorithm design and evaluation | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/2177d398df9d0b61c895579de1b257077d1cb424/2-Figure1-1.png)
PDF] AES-512: 512-bit Advanced Encryption Standard algorithm design and evaluation | Semantic Scholar

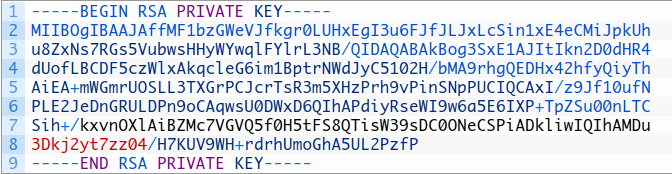
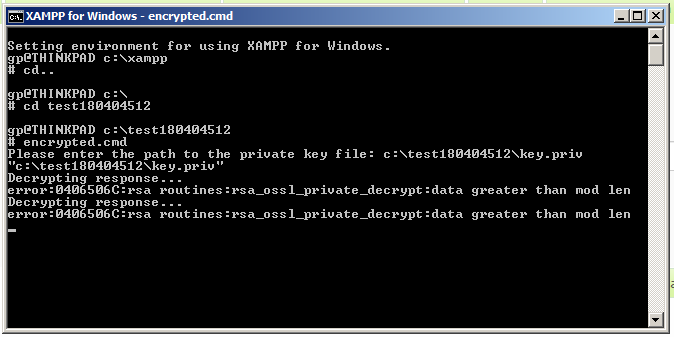
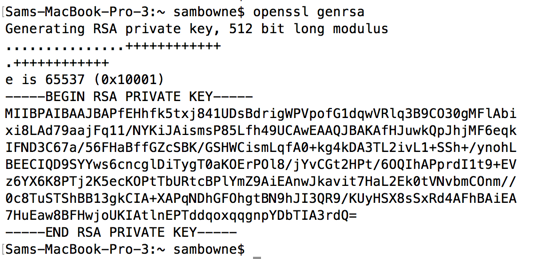
I have to crack a 512 bit RSA public key and get the private for a CTF, having a hard time figuring out the tools to use : r/HowToHack

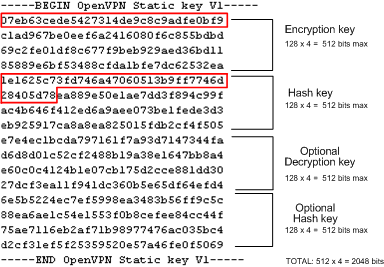
![PDF] AES Algorithm Using 512 Bit Key Implementationfor Secure Communication | Semantic Scholar PDF] AES Algorithm Using 512 Bit Key Implementationfor Secure Communication | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e8ff102e130ccdfa1054059a4da33d9cd1089fd0/3-Figure1-1.png)



![PDF] AES Algorithm Using 512 Bit Key Implementationfor Secure Communication | Semantic Scholar PDF] AES Algorithm Using 512 Bit Key Implementationfor Secure Communication | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e8ff102e130ccdfa1054059a4da33d9cd1089fd0/6-Figure4-1.png)





![PDF] AES Algorithm Using 512 Bit Key Implementationfor Secure Communication | Semantic Scholar PDF] AES Algorithm Using 512 Bit Key Implementationfor Secure Communication | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e8ff102e130ccdfa1054059a4da33d9cd1089fd0/4-Figure3-1.png)